 Check sheet
Check sheet
Why use it?
To allow a team to systematically record and compile data from historical sources, or observations as they happen, so that patterns and trends can be clearly detected and shown.
What does it do?
- Creates easy-to-understand data that come from a simple, efficient process that can be applied to any key performance areas
- Builds, with each observation, a clearer picture of “the facts” as opposed to the opinions of each team member
- Forces agreement on the definition of each condition or event (every person has to be looking for and recording the same thing)
- Makes patterns in the data become obvious quickly
How do I do it?
- Agree on the definition of the events or conditions being observed.
- If you are building a list of events or conditions as the observations are made, agree on the overall definition of the project.
- Example: If you are looking for reasons for late payments, agree on the definition of “late.”
- If you are working from a standard list of events or conditions, make sure that there is agreement on the meaning and application of each one.
- Example: If you are tracking sales calls from various regions, make sure everyone knows which states are in each region.
- Decide who will collect the data, over what period, and from what sources.
- Who collects the data obviously depends on the project and resources. The data collection period can range from hours to months. The data can come from either a sample or an entire population.
- Make sure the data collector(s) have both the time and knowledge they need to collect accurate information.
- Collect the data over a sufficient period to be sure the data represents “typical” results during a “typical” cycle for your business.
- Sometimes there may be important differences within a population that should be reflected by sampling each different subgroup individually. This is called stratification.
- Example: Collect complaint data from business travelers separately from other types of travelers. Collect scrap data from each machine separately.
- Design a Check Sheet form that is clear, complete, and easy to use.
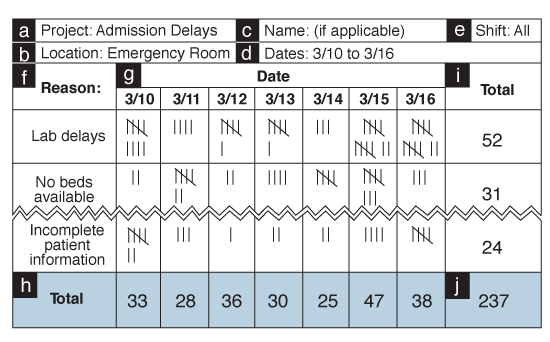
- A complete Check Sheet, illustrated below, includes the following:
- Source Information
- a Name of project
- b Location of data collection
- c Name of person recording data, if it applies
- d Date(s)
- e Other important identifiers
- Content Information
- f Column with defect/event name
- g Columns with collection days/dates
- h Totals for each column
- i Totals for each row
- j Grand total for both the columns and rows
- Source Information
- Collect the data consistently and accurately.
- Make sure all entries are written clearly.
Variations
Defect Location
Shows the concentration of defects by marking a drawing of the product each time a defect is found.

Task Checklist
Tasks in producing a product or delivering a service are checked off as they are done. In complex processes this is a form of “mistake proofing.”

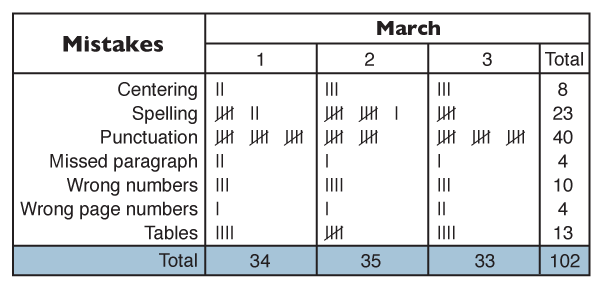

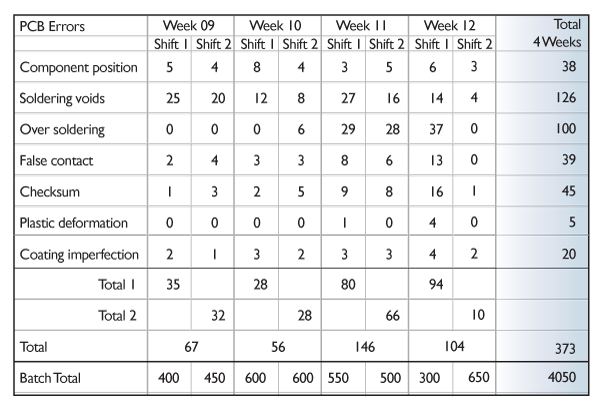
NOTE: This report needs to be accompanied with information of corrective actions taken as a result of numbers deviating from the norm.
At the production level, similar sheets are used to register the actual events as they happen. As soon as these numbers reach a threshold value, an action is initiated to investigate and correct the issue.

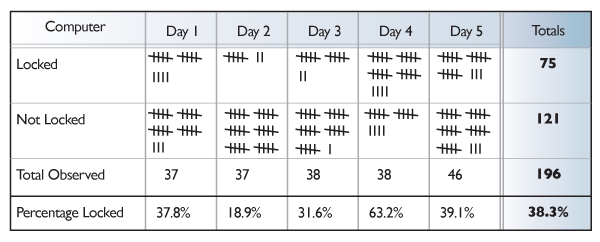
NOTE: As part of our ongoing efforts to monitor HIPPA and confidentiality requirements, a study was conducted to assess compliance with user workstations (computers) being locked when unattended in the office.